Cyber World
SIMULATION WEB GAME
Role
Lead Designer
collaborators
Lukas Zirngibl (Team lead)
Roman Burkard (Dev)
DESIGN GOAL
To empower users to gain valuable insights into diverse cyber threats, to foster a deeper understanding of evolving security challenges.
The project was research heavy and started with a deep dive into major cyberattacks. I identified and analysed the top 10-15 most impactful incidents, including the Melissa Virus, Log4j, WannaCry, and Stuxnet. To simulate these attacks, I developed detailed use cases, categorising them by timing, nature, perpetrators, impact, cost, and origin. I also focused on the technical aspects of each attack to understand the methods used. To gather visual inspiration for the game i used Midjourney to level up my creative narrative. I used GenAI to help refine my creative storytelling.
The concept is inspired by a flight simulation, cyber video games and space movies. The player is placed in the position of a spaceship. Different statistics provide information on the outside environment and ship data. In this simulation, the ship goes on an expedition flight to explore new planets.
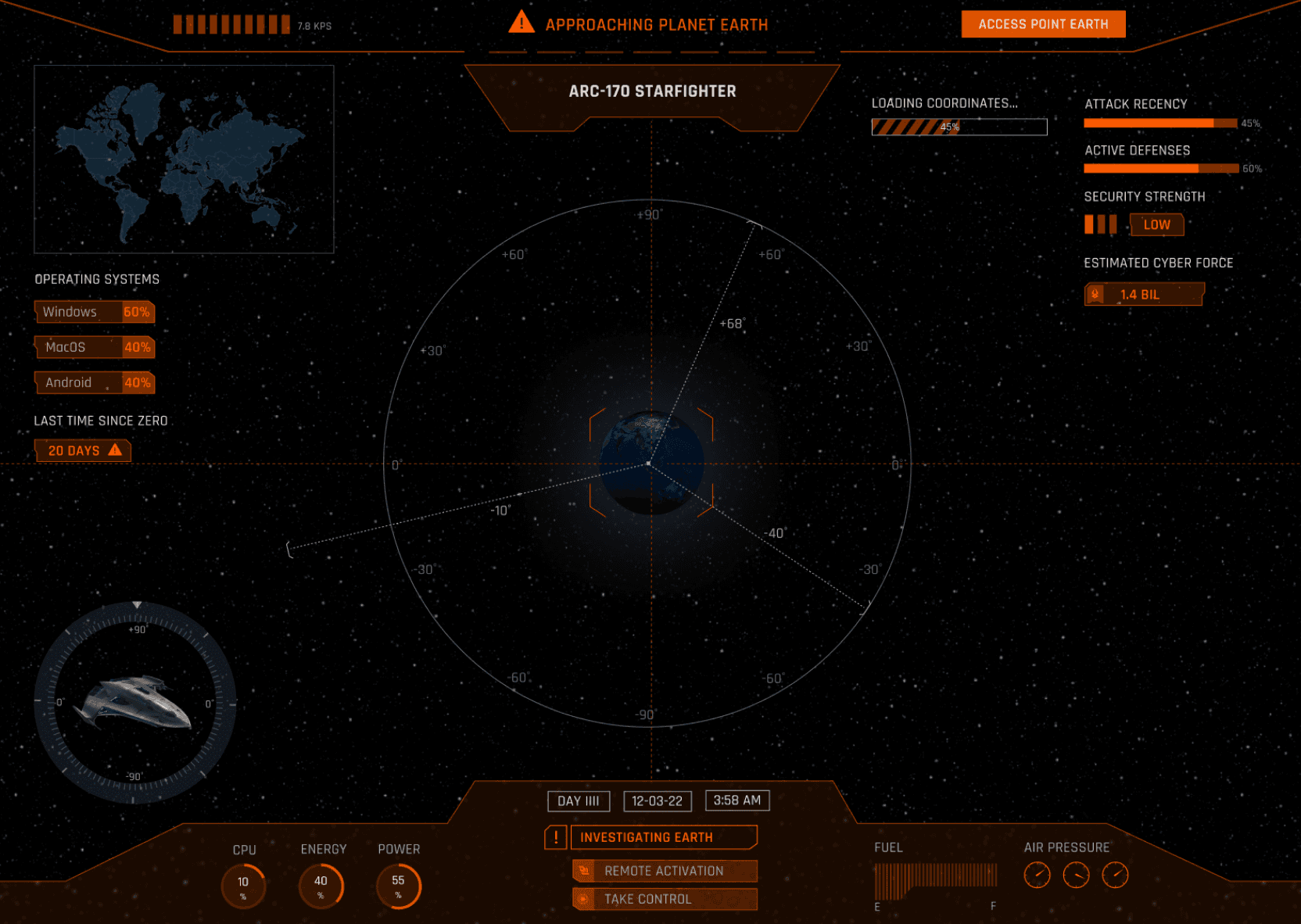
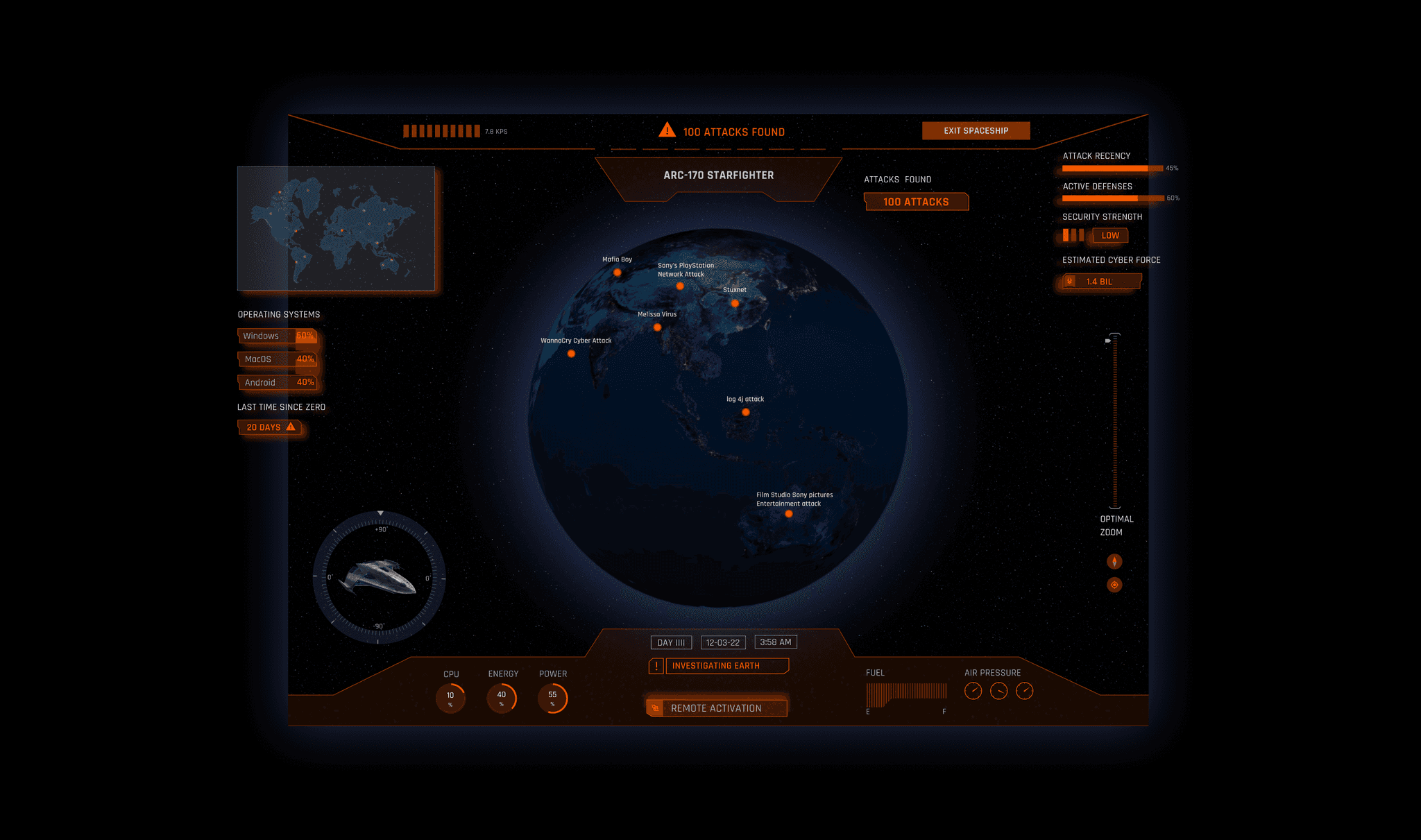
Once earth is found, earth coordinates are loading and positioning. The earth gets scanned for viruses and cyber attacks. Here, users can start the simulation game and explore different cyber attacks pointed out on earth. This cybersecurity prototype introduces a unique platform for users to explore an extensive archive of cyber attacks. This interactive tool empowers users to gain valuable insights into diverse cyber threats, fostering a deeper understanding of evolving security challenges.
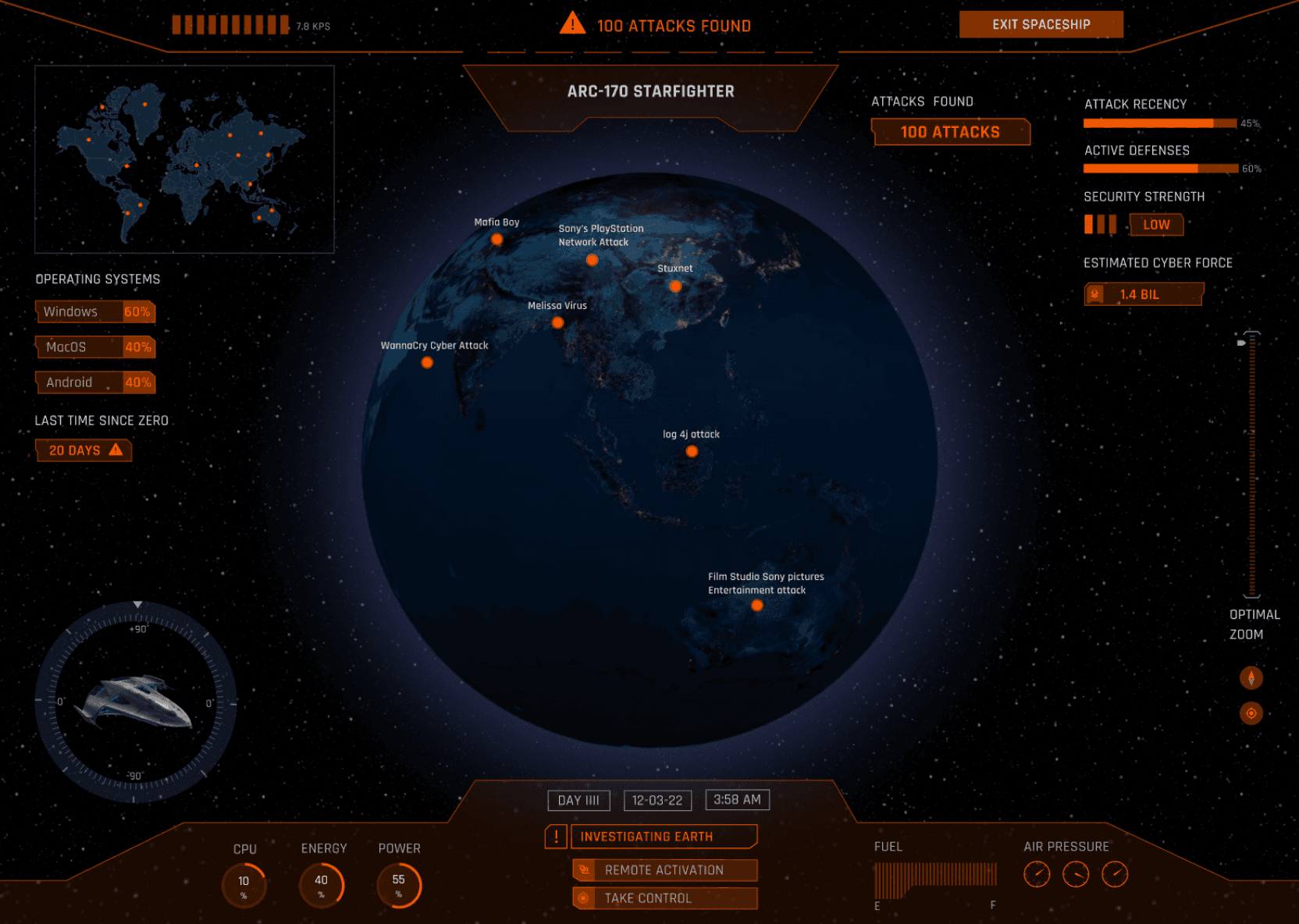
The user has launched the expedition and can now explore different cyber security attacks on planet earth by clicking on one of the orange attack point. The prototype offers a user-friendly interface, allowing individuals to navigate and analyse historical cyber attacks with ease. Through detailed case studies and interactive visualisations, users can dissect attack vectors, methodologies, and mitigation strategies, enhancing their overall cybersecurity awareness.
Once the user has selected an attack on earth, they can see high level facts of the simulation to a preview of the simulation. This example shows the Log4j Attack. One of the most severe cyber attacks worldwide. This hands-on approach facilitates a proactive stance against potential threats, equipping users with knowledge to bolster their digital defenses.
Different categories are covered such as when, where, what, intention, severity and estimated costs. A special focus is placed on the technical explanation of how such an attack has been realised.
As cyber threats continue to evolve, our prototype serves as a valuable resource, arming users with the information needed to stay ahead in the ever-changing landscape of cybersecurity.
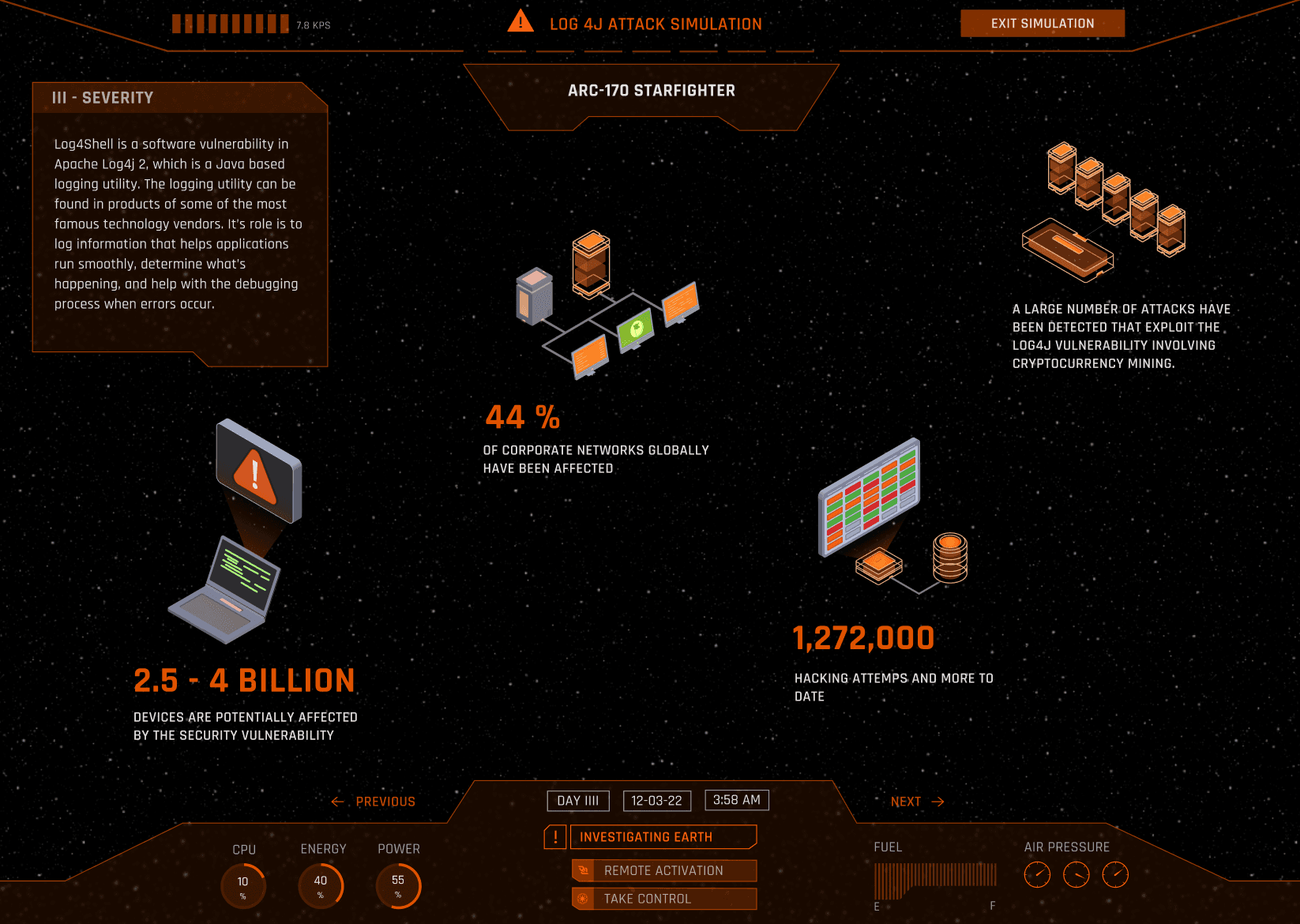
Facts and statistics undermine and explain the severity and extend of the attack based on the research conducted in the case studies.
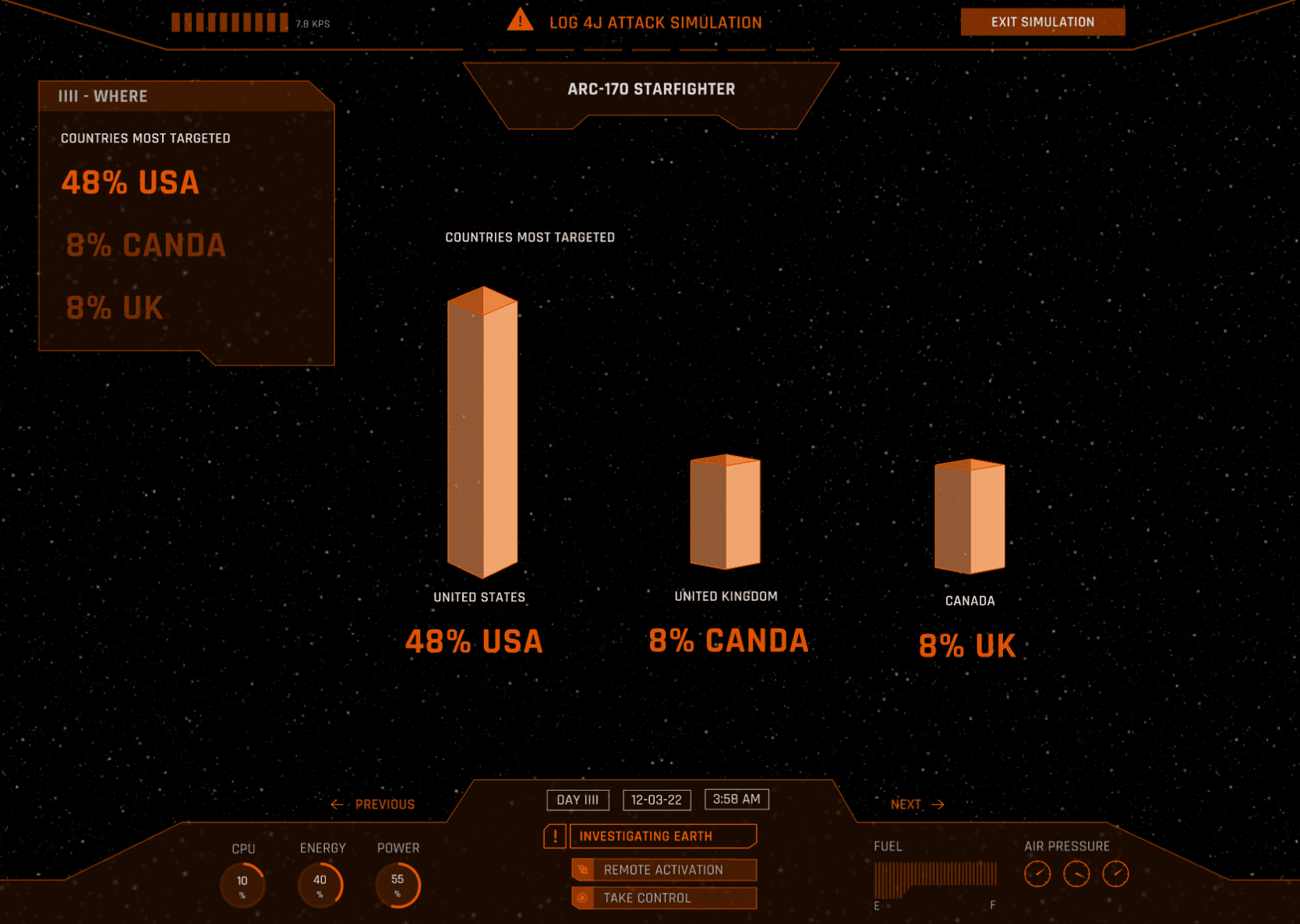
As cyber threats continue to evolve, our prototype serves as a valuable resource, arming users with the information needed to stay ahead in the ever-changing landscape of cybersecurity.